In today’s digitally reliant world, cyber security has never been more important. A cyber-attack can have disastrous consequences – from outages and downtime to data loss and reputational damage. With 84% of businesses experiencing a malicious attack in the past 12 months[1], it is no longer a question of ‘if’ but ‘when’ an attack will happen. Is your business prepared?
Business must plan to protect AND recover
Many businesses have a belts and braces approach to mitigating risks and protect their network with the relevant software, processes and procedures – however they fail to fully prepare to recover in the event of a breach believing that an attack simply will not penetrate their defences.
Recovering from a business outage or attack is much more than being able to identify and invoke defence mechanisms. Given that 92% of cyber-attacks result in data corruption or loss, too many businesses fail to consider their response and recovery strategies which are critical components in minimising the effect of an attack.
The need for a busines-wide cyber security culture
Cyber security is an investment – not only in software and applications within your IT infrastructure, but within the internal processes and culture. Whilst software such as malware detection, backup and data replication will protect the business technically, it is also critical to implement process and procedures in the event of human error and to ensure your business has a security centric culture in place. For example: whether this is colleague training on awareness of phishing attacks through to challenging visitors into secure offices without credentials. The ability to protect and recover from an attack or outage must be a business wide consideration.
Cyber security framework: How prepared area you? 5 steps to protect and recover
Businesses need to be prepared and have a continuity strategy outlined in the event of an attack or outage, with equal emphasis placed on recovery as detection. The 5-step cyber security framework, developed by NIST(2), outlines the stages to take in helping prepare and mitigate when attacks occur to ensure you can get your business back up and running as quickly as possible with minimal downtime and disruption.
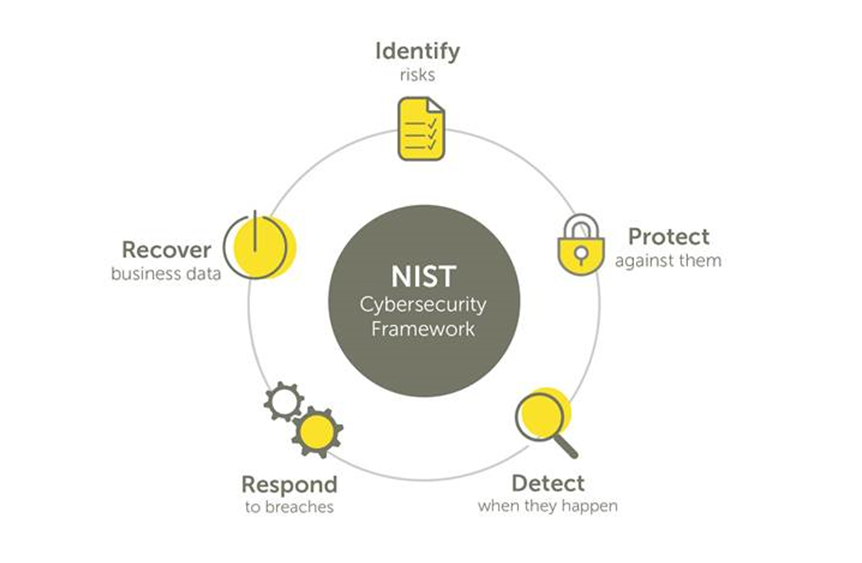
-
Identify risks
Gain an understanding across the business to managing cyber security and risk to systems, people, assets, data, and capabilities to identify what process, polices, software etc need to be put in place.
For example: Identifying all physical and software assets within the business and level of protection
-
Protect against them
Develop and implement appropriate safeguards to ensure critical infrastructure and data can be protected in the event of an attack.
For example: Implement a cyber security policy that includes risk management and governance with secure processes and procedures such as access controls, duo-authentication sign in and background checks. Ensure policies are trained out to all.
-
Detect when they happen
Through implementation of software and processes which identify attacks.
For example: Install DDoS projection and firewalls to secure your network. Undertake employee awareness and training on attacks and the process to invoke when this occurs.
-
Respond to breaches
Create a plan for disaster and information security incidents.
For example: Failover systems in place, appropriate Recovery Time Objectives (RTO) that ensure you systems can restore systems and applications, meaning your business can get back up and running. Clear communication plan to the business and any impacted customers.
-
Recover your data
Implement recovery plans to ensure business continuity.
For example: Recovery Point Objectives (RPO) that ensure your data is backed up/replicated and can be recovered appropriately. Clear communication plan to the business of process and accountabilities.
How M247 can help
Disaster Recovery as a Service: Powered by market leader Zerto, our Disaster Recovery as a Service (DRaaS) solution enables you to roll-back to a previous version before an attack has encrypted your files. With industry leading RPO and RTO times (which rollback to just minutes prior to an attack) you’ll be able to restore your business immediately, avoiding ransom demands and ensuring your customer experience or business performance are not affected.
Business-critical security solutions: Whether you are looking for firewalls, managed DDoS protection or content filtering our range of security options can be tailored to offer your business powerful protection. Designed to work together in almost any combination, as single solutions or as a complete package, and all underpinned by ISO27001 Security Standard.
For more information on either of these services please get in touch.
[1] Business Resilience Readiness Thought Leadership Survey, IDC, May, 2019 https://www.nist.gov/





